Traditional IT network security trusts anyone and anything inside the network. A Zero Trust architecture trusts no one and nothing.
Clientside encryption and decryption. Payload encryption (AES-256), Key encryption (RSA-4096), Transport authorization (TOTP), Transport encryption (TLS)
No hidden and shady stuff going on behind the scenes. Entire code and all mechanisms fully transparent and peer reviewed.
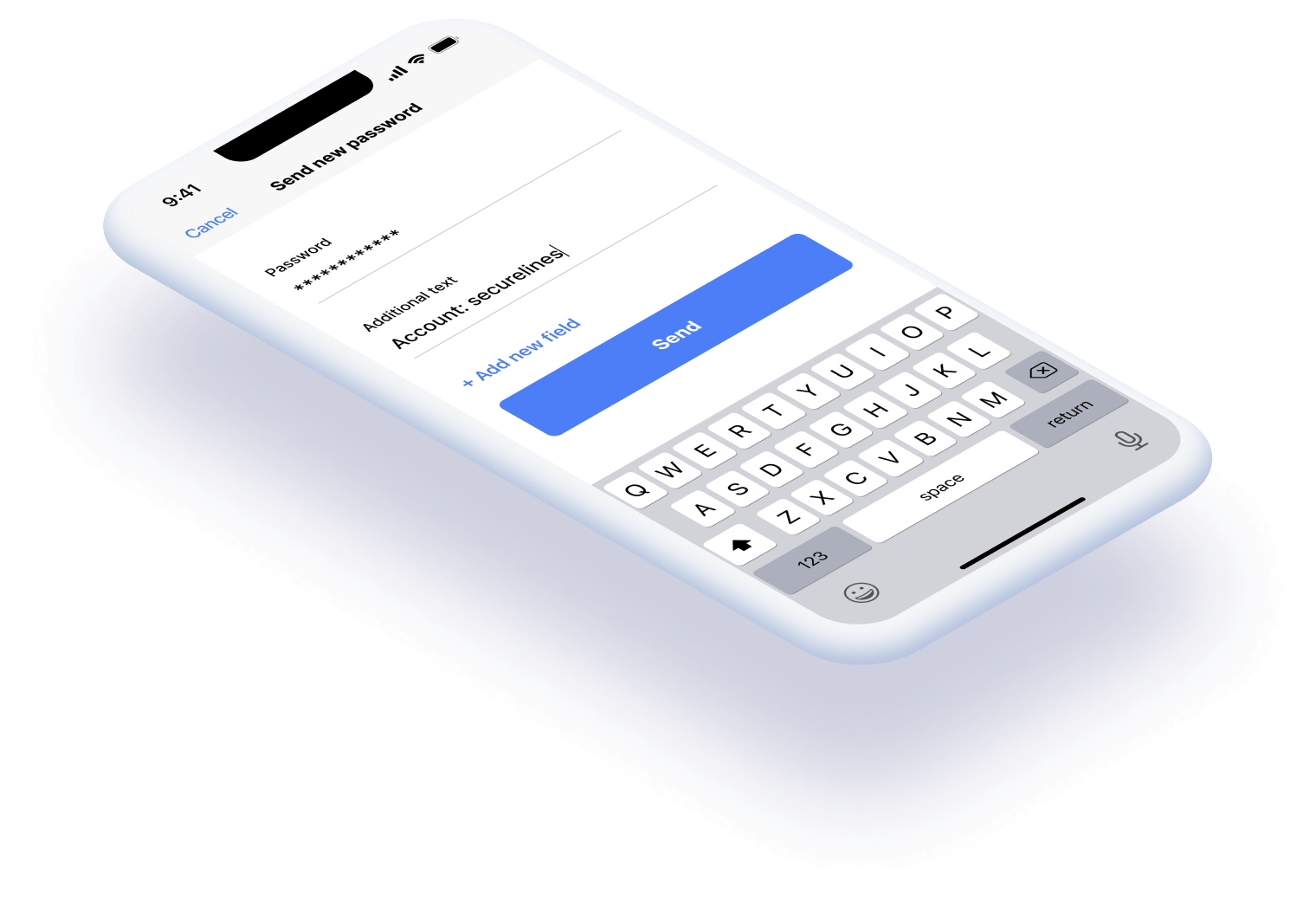
With Secure Lines you never have to worry again when sending passwords. And it’s so easy, even your mum can use it.
“Secure Lines is on another level. We are sharing all kind of sensible data on a daily basis. For us it’s a game changer! 👍🏻”
“Finally an open source password exchange that I really like! I’ve already onboarded several colleagues and everything went smoothly as it should.”
“The best password sharing app out there. Love how easy and simple the process is.”
“I would highly recommend Secure Lines if you are sharing passwords, API keys and other sensible stuff.”
Yes, Secure Lines only comes with a free version. 0 costs, but 100% secure.
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access a resource. Zero trust is best known from network architectures but still it is a holistic approach. Secure-lines uses this approach and adds extra and extensive encryption layers. This enables secure lines to not only guarantee the identity of the persons communicating but also to trust the contents exchanged.
Secure lines trust nobody, not even ourselves. This is why not even we can access the data exchanged between secure lines and that’s how secure your most pressures keys and passwords are.
But be aware, if you loose your device not even we can recover your data.
A short summary of the principal mechanism of Secure Lines
1. Clientside encryption
2. Encrypted (TLS) to a delegation server (TOTP) and encrypted again from the delegation server (TLS)
3. Clientside decryption